March 31, 2015
I. Executive Overview / Introduction
We live in an increasingly digital world where technology changes quickly and the only recognized absolute is there will be more data to manage tomorrow. The unprecedented growth of content, combined with complex regulatory and legal obligations and ever-increasing pressure from the business to do more with less, has left stakeholders across the enterprise bewildered about how to respond. Although organizations increasingly recognize the need for an information governance (IG) program to address these challenges, most do not know where to start.
Unfortunately, the problem is not going away. Procrastination only makes it worse as the Volume, Velocity, Variety (the three V’s) of data continue to grow. Add mobile computing to the mix along with worsening cyber security threats and you have a perfect storm. (This topic was examined and some of the key IG challenges highlighted in an earlier EDRM paper entitled “Disposing of Digital Debris” – We invite you to explore that paper.)
This paper is the first in a series that goes deeper to examine and understand the specific stakeholders in information governance.
The Information Technology (IT) department is a critical stakeholder in any Information Governance initiative because IT manages or has some responsibility for the vast majority of information in an organization. While traditionally this function focuses on technology, infrastructure and storage, now it must also align with the business and its objectives and the specific value of information.
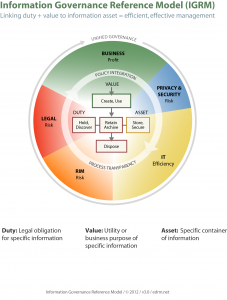
On the following pages we will explore the role of IT as a key stakeholder within the Information Governance Reference Model (IGRM) framework (see below). Being an effective stakeholder requires a two-way flow of information. So in this paper we will cover both IT’s responsibility to other stakeholders and what IT should expect in return. We will also consider the benefits IT can receive from collaborating to create a well-executed IG program. The basis for the following commentary is the IGRM created by EDRM. It helps identify the information stakeholders, defines the nature of their stake in information, links information value and duty to information assets and highlights the interdependence across the stakeholders. The model is designed to help organizations navigate the complex landscape of information governance.
Given the information governance challenges organizations face today, the IGRM serves as a foundation to build a strategy to help take that first step towards action. Now let us begin to analyze the role of IT as a key stakeholder in any IG program.
II. The IGRM Model
To achieve unified information governance, the IGRM model designed by EDRM provides an intellectual framework which advocates policy and process integration across information stakeholders: mainly IT, Business, Legal, Records and Information Management (RIM), Security and Privacy.
This integration is designed to bring process transparency to stakeholders so they can see what value and duty exist against information assets at any point in time. They can then perform their functions against these assets without adding unintentional risk to the organization. The model facilitates communication and cooperation among stakeholders, drives cross-functional processes, and aligns information governance goals across the organization so real results can be achieved.
Because bringing stakeholders to the table and working through information governance issues can be difficult in practicality, it is vital to start from a coherent framework of ideas like the IRGM model. The ultimate benefit is keeping valued information securely within the organization, cutting information cost and reducing its risk to the organization, and disposal of low value information.
To address IG, many companies create a cross-departmental coordinating structure, such as a group or committee with key stakeholders, which report up to an executive steering committee that includes the GC, CIO, CFO; and IT is a core stakeholder in any IG coordinating structure.
III. IT as an IGRM Stakeholder
We define IT broadly since there is a multitude of IT-related specialities ranging from database management to hardware installation to content and records management, application deployment to support. Consequently, IT itself divides into sub-stakeholders each of whom may need a place at the table beyond just the CTO or CIO, such as the leader of the data storage or messaging infrastructure groups.
IT also is a discipline that ranges in scope from being very centralized, to being in the hands of individuals in the business units throughout the organization. In addition, the balance of behind the corporate firewall data and applications to outside cloud-based or outsourced functions will vary. What IT is, therefore, varies considerably from entity to entity.
IT is a critical stakeholder because traditionally IT has run and secured the network in which corporate data resides and managed the applications and hardware used for businesses that generate data. IT also secures and stores legacy data from the organization. Increasingly, IT responsibilities intersect with Corporate Information Security (CIS), Privacy, Records Information Management (RIM) and the demands of the legal department.
A. Key Considerations to Understand IT as an IG Stakeholder
IT’s responsibilities at the broadest level usually include where and how, but not what information should be maintained or why or how long. The business units should largely determine what and why, legal and compliance how long. In reality, these questions are interrelated. All too often there is a lack of clear direction from these other stakeholders, so IT makes decisions by default about information. These decisions may add information risk to the organization as information with legal or regulatory duty might be deleted, or kept longer than it should.
The following are some characteristics of IT concerning its growth, complexity, and responsibilities that other stakeholders should try to understand:
- IT has many, growing, complex and disparate responsibilities and can be overwhelmed by business demands, proliferation of applications, including mobile and social applications, the exponential growth in data volume, types and locations and increasing data security threats.
- IT and CIOs hitherto have addressed spiralling data volumes by applying several standard tactics at the data layer: compression, tiering, off lining, de-duplication and virtualization, some of which are no longer sufficient. No single standard in and of itself provides a sufficient solution, but rather a combination of these is required.
- Without guidance from business units about what data to delete, the response of IT to exponential growth in unstructured data has often been to acquire more storage capacity which is perceived as simple and monetarily cheap. This storage “habit” can be an obstacle to full engagement in what is perceived as a complex, long term IG initiative.
- In the frequent absence of clear guidance from business units or the organization as a whole, IT often develops a culture of keeping all data just in case it is required. This practice increases risk and conflicts with requirements of defensible disposal that are at the heart of Information Governance. For example, some privacy laws — such as the Health Insurance Portability and Accountability Act in the United States and the Data Protection Directive in the European Union — actually require the deletion of certain types of information after a period of time.
- In the age of digital transformation, data drives the business direction and outcome and to a large extent is the business. Consequently, IT plays an increasingly integral role across many departments, from operations and finance to marketing and human resources. In particular, IT is increasingly expected to support sophisticated analytics tools to “big data” to deliver business insight and value but often without additional resources. This is a new and complex responsibility falling considerably on the CIO and IT department.
- With the addition of cloud to the mix, there are various degrees of hybrid deployments IT must manage spanning from complete on premises or behind the corporate firewall deployments to almost complete reliance on the cloud to store data and run business applications.
- Mobile computing stresses the ability of IT to fulfill their core functions, determine appropriate Bring Your Own Device (BYOD) policies and implement all necessary supporting infrastructure. The majority of corporate work is now conducted on mobile and portable devices like smart phones and tablets, over half of which belong to users and not the corporation. Also, the trend is for more work to be conducted out of the office than in the office but users still demand unrestricted access to data. These trends greatly stress the resources of the IT department.
- With mobility come more collaborative and social users. Mobile workers would like to create, add, and collaborate on documents on the go and would like to have all social capabilities. IT has to provide this capability within and outside the firewall in a secure and collaborative way, such as transforming shared network structures into social and collaborative document management systems.
- In the absence of an organization-wide IG program some business units chart their own course without IT by bringing cloud-born applications into the organization’s firewalls to meet pressing needs. Consumerization of technology and the increasing technology literacy of the users make this possible. This self-service “shadow IT” by business units adds more pressure on the IT department.
- The organization as a whole may view IT as largely a cost center or a service organization, rather than a core stakeholder making business possible or a strategic partner that can deliver critical business insight to the business units.
- Traditionally most CIOs have little responsibility for or ownership of information, but almost complete responsibility for the infrastructure – that which that houses information. The resulting cognitive dissonance makes solving the IG problem more difficult.
- IT often lacks the legal and regulatory background or clear guidance from other stakeholders to link compliance obligations to the thousands of applications, databases and other data repositories which it manages.
B. Conflicting Requirements
IT often faces apparently conflicting requirements from other stakeholders and lines of business that a coherent IG framework must help resolve. For example:
- The business unit’s desire to share information may conflict with Security’s desire to protect, Compliance’s desire to preserve privacy, and IT’s ability to secure information with a reasonable level of administration.
- The legal department’s desire to preserve content and versions of documents (particularly if it is not relevant to litigation) may conflict with the lines of businesses or Record Management’s desires to dispose of lesser value or superseded content.
- The value of data for IT largely relates to its technical value, which changes rapidly, rather than its business value. However, the age or type of data is typically not as much of an indicator of relevancy for other stakeholders.
- IT often views the legal department as too risk-averse regarding the disposal of information. Legal often views IT as not providing the tools, infrastructure and other resources needed to gain visibility into data and make responsible determinations about what to keep or dispose.
- RIM may be mostly concerned with classifying and storing records or the data visible to and used by the users, while failing to understand the demands and complexity of the underlying data and applications which are the enormous submerged iceberg of the data.
In short, the IT world is increasingly complex and demanding while resources remain limited. Let’s see what IT supplies to the information stakeholders and in turn what IT demands from their peer stakeholders to perform well in a healthy IG paradigm.
IV. What IT Provides to an IG Initiative
IT supports the operations and security of the entire organization and is therefore vital to any Information governance effort by delivering the following:
A unique horizontal perspective – Because IT works with all vertical business units or silos, it can bring a unique horizontal view across the organization that can provide a valuable perspective to an IG initiative.
Information cataloguing – Understanding and documenting the location of different categories of information in the organization benefits many stakeholders within an organization. The responsibility for creating and maintaining a data map falls to IT since they often have the best technical understanding of where this information is physically held.
Thus Legal needs to know where to look to find responsive data for litigation. Records management needs to apply retention policies and schedules. The compliance group focuses on where risky data should and should not be held and under what legal requirements. The business knows the value assigned to information created by line of business applications or group of users. The organization needs this information in the information catalogue so that they can manage it based on its true value.
Provisioning systems – Many information systems from Enterprise Resource Provisioning (ERP) to content and records management manage information in a way that can benefit the other stakeholders in the IGRM model. IT usually takes in provisioning information systems to the enterprise, usually a suite of integrated applications — that a company can use to collect, store, manage and interpret data from many business activities. It is their role to solicit requirements and balance conflicting imperatives in the design and roll out of technology.
Once an IGRM discipline is set, moving forward provisioning could simply take the corporate standards into consideration. For example, jurisdictional regulatory obligations, security, privacy, and line of business (LOB) service level agreement (SLA) requirements determine what types of systems to provision.
Managing active information assets – IT manages active information assets and this includes putting a unified content management system in place, managing information based on its value, allowing mobile, social users to create and collaborate on information anytime, anywhere, on any device, from within processes or from their social environments, within or outside the firewall. IT is also responsible for appropriate redundancy in technology, disaster recovery planning, appropriate backup and recovery technologies and practices
Acceptable Use, BYOD, and other information management policies – Establishing controls on the use of organizational IT assets is a critical role for IT. IT often can apply controls without even having a written policy in place. As long as IT is responsible for establishing and supporting information technologies, they will supply an important and unique perspective in defining what these policies should be. At the same time, IT should support and not break the rules from Legal, Business, Records, and Privacy and Security stakeholders.
New initiatives in the cloud – Today, business deployments range from purely cloud to purely on premises and anything in between. Cloud deployments do not lessen any of the information governance responsibilities but bring in new complications: organizations have to know the laws and regulations restricting the collection, storage, processing, disclosure, and movement of information. IT has the lead role in collaborating with line-of-business users to set the governance initiatives expected from the cloud provider and the organization to ensure information is governed whether it is in the cloud or on premises. Whether applications are chosen by the LOB in the cloud or developed within the firewalls, someone needs to have an information catalog across the organization to enable the organization function effectively.
Unified content access – With many sources of information being created on premises and on the cloud, it is IT that provides critical access to information in a unified fashion without having to remove existing content and replace. Unified access, information consolidation, and information migration from multiple sources may all be required. Although one does not need physical consolidation to have unified information access, IT can implement physical consolidation to eliminate unnecessary cost and modernize existing systems to serve LOB faster in areas such as social and mobile adoption. IT can also bridge the gap between structured to unstructured information management as both are just “information” to run the business from LOB perspective.
Technology standards – The application of technology standards varies from organization to organization and changes over time but usually falls on IT. These standards can range widely, covering software, languages, protocols, operating systems, security, storage quotas, hardware interfaces, and so on. The purpose and point of standards is to reduce costs, maximize accessibility, increase interoperability, and meet the business needs that come from the various organizational imperatives reflected in the IGRM model.
Information and network security – IT provides leadership for the proper protection and authentication of data and its availability for use, preservation, and disposition. In the present high-threat environment and against the background of numerous high-profile data breaches, the function of IT in securing data is more important than ever and IT resources are stretched thin. Data security is complex and requires policy, process and technology. IT may not always set overall data security policy but it deploys hardware and software and implements policy, sometime ad hoc policy, as well as responds to threats to the corporate data.
Managing archive and/or legacy information assets – Only a small percentage of legacy information falls to Records Management for definition and control. According to Compliance Governance Oversight Council (CGOC), only 5% of information is considered records; the rest is less visible or “submerged” to users and not considered records. However, much of the information can create cost and potential risk to the organization if not governed properly. Legacy information resides on technologies and in systems mostly supported and maintained by IT. IT principally contributes an understanding of the costs for keeping this information and maintaining reliability and security. Once information loses its value to the business and meets its obligations, it should be removed before it becomes dark data adding no value but increasing cost and risk to the organization.
Decommissioning and disposal – Managing license fees for various enterprise software often falls under IT’s domain. For example, when a strategic decision is made to align on a particular platform or product, or if a system or technology no longer meets the business needs, that often often mean decommissioning a number of other products or systems. The decommissioning process is an IT task, but it needs to ensure the responsive litigation is preserved, and records retention rules are not broken.
Overall, when IT has visibility into the value of information assigned by LOB and duties assigned to information by Legal, Records and Information Management (RIM), and Privacy officers, IT can manage information assets based on its total value and duty and plan to safely disposing remaining data. This is the foundation of any successful IG initiative.
V. What IT Requires from Other Stakeholders
In order for IT to perform the above functions well, it needs cooperation and input from other information stakeholders, particularly the ones who assign value and duty to the assets. The role of IT in this situation is to take the business requirements about the valuation from these stakeholders and connect them to technology infrastructure, standards, procedures and processes, automating these processes to the extent possible.
IT usually does not nor should it take primary responsibility for determining, representing, or defending these requirements in the first place. IT can, however, catalogue this information along with other data as stakeholders define the value they give to information they create.
Value assigned to information assets – IT owns the systems that the organization uses to create, use and store information. That means they own the bits and bytes. But they do not own the ‘information’ or usually understand its meaning to the business, beyond who created it, what system is used, and various other derived characteristics. Furthermore, IT may have only a limited idea of what data might be useful in a given business context.
The business units know what business value they expect from the information produced. However, this value mostly is not captured in any of the corporate systems but stays locked in the minds of business units. This gap begs for an organized way for business units to communicate the true value of their information assets so IT can manage those assets accordingly.
Duty assigned to information assets – There are an increasing number of regulatory and legal duties attached to data in an organization that must exist in an IG framework:
- Legal department determines what information to place on litigation hold, what information to include in an e-discovery requests, and what processes and policies to put in place for defensibility. IT needs Legal to define the scope of e-discovery and could give the Legal department technology support, starting with information asset cataloging, preservation and often data collection.
- Privacy and Security groups determine what processes should protect the company and its assets, and control access to only required sites based on responsibility levels, roles, etc. Compliance should clearly state privacy rules so that IT can secure information based on these rules. IT does not define what the rules are but requires this information from privacy and security leaders.
- Records and Information Management (RIM) is responsible for leading, planning and managing the corporate records management program. Key to this role is keeping senior management informed on current and projected operational requirements, legal obligations, compliance issues and regulatory matters. This set of responsibilities will typically include a catalogue of relevant laws including geopolitical jurisdictional differences with clear guidance on how to manage information assets based upon their physical location. This results in defined requirements specific to the statutes and laws of each particular jurisdiction where the organization conducts business.
- Critically, IT must know this information to properly manage data on its systems. With this input, IT can conduct proper disposition of information assets wherever they reside. RIM and IT must apply these definitions across all content, including all information within applications, on backup systems and tapes, in the cloud or on-premises and independent of whether they are official records or non-records. Applied correctly, the result is maximum reduction of cost and risk mitigation.
- The business units should inform IT about information being created, what type of content, and for what purpose information is collected. The business input together with records, privacy, and security requirements must give IT sufficient information about the obligations attached to information assets. IT in turn can then apply policies and enforce their execution on information assets. Establishing automated execution with audit trail and traceability can give maximum defensibility when required.
Clear policy and rules that can be implemented – The IT department needs clear rules to implement, not shades of grey or judgment calls that are the responsibility of business units. Policies and processes defined by the stakeholders allow IT to manage information in alignment with these rules.
Executive support of the IG initiative – IT requires the highest level of executive C-level support possible for the information governance initiative; IT cannot expect to drive an IG effort alone. IT also needs the support and assistance of Legal, Compliance, Security, RIM and the LOB. The closer these departments are in their efforts and the more aligned they are with the business processes, then the more successful IT and the organization as a whole will be in achieving its information governance plans.
Achievable milestones within overstretched resources – It is axiomatic that in the present business environment there is simply more for IT to do than resources allow, particularly given increased cybersecurity threats and the exponential growth of data, data types and data stores. Therefore other stakeholders need to adopt realistic expectations for IT to implement information governance objectives, and even provide staffing and budget resources where possible.
IT requires a series of achievable steps, usually starting with mitigation of the largest risks. Information governance cannot be managed all at once, and IT functions need to be put in a coherent plan and designed to show a series of prioritized, achievable, measureable successes.
VI. The Benefits of IG to the IT Department
It is only with a robust information governance program and structure, policies, processes, and technologies in place that IT can perform its essential functions within the organization without creating excess information cost and risk to the organization.
Within an IG framework IT can better prioritize work and assign resources. Specifically, the ability to finally dispose of information is critical to the success of IT as a department and reduces cost and risk. This is only possible defensibly within the context of an IG program. Effective information governance allows for appropriate disposal of data, means less money spent on storage, and facilitates proper management of legacy data.
This likely means extra budget for IT to engage in IG. It may also mean the organization invests in big data analytics that improve revenue, provide value to the organization and enhance the role of IT in the organization. With an IG system in place the CIO and IT department can better contribute to the growth of the business and engage in new and exciting areas such as “big data” analytics, social, cloud, and mobile transformation. In other words, with IG then IT moves from an “order taker” to an “order maker”.
More specifically, with a well-designed and executed IG program, including the tools necessary to index and analyze existing content collections, IT will be able to achieve the following kinds of key technical objectives:
- Map information assets to owners to policies and processes to enforce information governance execution on assets.
- Take unstructured data, filter it, index it, and apply policies based on the specific needs of one’s organization, turning it into structured information of value.
- Plan for level of effort and infrastructure requirements including on-premises, cloud, and hybrid cloud deployment models.
- Understand technical architecture needs including:
- Email and PST, NSF in uncontrolled environments
- Database creation, access, and protection
- Application development for desktop, web, mobile of any sort
- Social, mobile, and collaborative information engagement tools
- Hybrid cloud deployments and soon the Internet of Things.
- Align policy and practice definitions with information governance policy and processes, specifically:
- Information retention not only for records but all information assets
- Information governance based on the actual content and business value defined by the business users rather than just “we have always done it that way” type of best practices
- Duties against information defined by legal, privacy, security, and regulatory obligations
- Tiered storage management requirements at the lowest architecture level, including requirements such as WORM and required standards for deletion.
- Enable the ability to split, merge, or cloud-enable content based on business needs.
- Identify enterprise content management design elements including:
- content types
- content capture methodology
- metadata usage and interoperability standards
- security including data at rest, data in motion, permissions, encryption templates
- unified content access, processing, and workflow
- multi-channel user engagement including mobile, social, and collaboration on any content type, on any device, anywhere, and anytime
- multiple OS storage systems.
VII. Call to Action – Suggested Actions for IT to Take
For the IT department initiating or being asked to participate in an information governance initiative the task can at first seem distracting or overwhelming. However, here are some simple guide points to help IT move forward:
- Seek out the IG stakeholders within your organization and begin to build the goals and criteria needed to better manage information. Communicate clearly where you have the responsibilities, need the appropriate criteria, and can add value along the way.
- Create a communications plan that allows for regularly scheduled meetings with channels of communications to the appropriate organizations and stakeholders. Set checkpoints and milestones that encourage cross-functional interaction and communications.
- Create an information catalogue or inventory; you have to know what you have in the first place. The business can then make fact-based decisions about governance concerns.
- Capture information value, assigned by the LOB, and put it in the information catalogue; that way, one can connect business value to assets and manage assets based on business value along with duties.
- Look for an enterprise content management foundation not only to bring control and security to unstructured content for internal users but to enable mobile and social users access content anytime, anywhere, on any device (on-premises, cloud, hybrid); file shares are not enough to manage content based on business value and duty.
- Reach out to RIM to put retention policies on information assets beyond traditional records; connect retention policies to assets.
- Help the legal department with the information catalogue; connect legal obligations and assets to ensure legal duties against these assets are met.
- Look for solutions that can connect policies to assets for automated execution for these stakeholders. Bringing stakeholders to the table could become easier once we have tools to bring their policies and processes together. Once you connect business value and obligations to assets, dispose of unnecessary information to reduce information cost and risk.
VIII. Conclusion
A successful IG initiative requires all the key stakeholders at the table long term, and IT is a vital stakeholder. Determining the value, purpose, access, privacy, security, and costs related to information assets requires input from all of the participants in the IGRM model. Other stakeholders need to understand the stressors and drivers that IT functions under in the present environment as well as the enormous value IT brings to the table.
Not having IT at the information governance table not only creates excess risk to the organization but also high cost as maintaining information with no value and duty increases information cost to the organization. Additionally, lack of participation and communications can cause inadequate technologies to be deployed and cause division instead of fostering a co-operative environment that enhances productivity and meets all requirements of the organization.
IT managing information assets without legal, records, business, security, and privacy viewpoints will likely raise the risk to the organization from legal and regulatory obligations perspectives. Ensuring IT is at the table of an IG initiative and fully supported in its efforts is vital to effective information governance.
The IGRM model provides a useful framework to make this possible.
In this ear of Big Data and digital engagement, bringing stakeholders’ perspectives together, what they provide and what they need from one other, are essential to establishing cohesive information governance. Policies and processes defined by these stakeholders married with technology available to operationalize and enforce governance execution on all information assets are required. Not surprisingly, it comes down to policy, processes, people, technology, and expertise.
IGRM has been adopted by many organizations to create a dialog between these stakeholders and pull together a governance program starting with the most pressing need. This process may go slow at first, but yield dividends long term. Without all stakeholders’ perspectives there is always some risk left at the table when it comes to information disposal.
IX. About EDRM
EDRM creates practical resources to improve e-discovery and information governance. Launched in May 2005, EDRM was established to address the lack of standards and guidelines in the e-discovery market. In January 2006, EDRM published the Electronic Discovery Reference Model, followed by additional resources such as IGRM, CARRM and the Talent Task Matrix. Since its launch, EDRM has comprised 320 organizations, including 186 service and software providers, 71 law firms, 47 corporations, 8 governmental entities, 4 educational institutions and 4 industry groups involved with e-discovery and information governance. Information about EDRM is available at https://edrm.net.