
[EDRM Editor’s Note: The opinions and positions are those of Sheila Grela.]
In today’s digital age landscape, where 27% of law firms experience security breaches, protecting sensitive client information is paramount for legal professionals. With cyber threats becoming more sophisticated, relying solely on passwords is no longer sufficient. There is an important acronym to add to your word vault – MFA – Multi-Factor Authentication (MFA) is a robust security measure that adds an extra layer of protection. For law firms, embracing MFA is not just a recommendation; it’s mandatory. You don’t have to be a geek to see the value and necessity of MFA.
Truth and wisdom in identity management is a collection of verification processes–the more you have, the greater your chances in defending your systems from cyber attacks.”
Justine Phillips, Partner at Baker & McKenzie.
What is Multi-Factor Authentication?
Multi-Factor Authentication (MFA) is a security method that requires the use of two or more authentication factors to verify a user’s identity before granting access to an organization’s network, remote email access, or privileged accounts. MFA ensures that users are who they say they are, helping keep data and business systems safe even if one set of credentials, such as a user ID and password, has been compromised.
Security is not a product, but a process.
Bruce Schneier.
MFA involves at least two of the following three factors:
- Something you know: A password or PIN.
- Something you have: A smartphone, hardware token, or access card.
- Something you are: Biometric verification such as a fingerprint or facial recognition.
During a recent presentation to the California Lawyers Association at the Small and Solo Summit, Amber Bevacqua-Lynott provided great advice. When a program or application asks if you want MFA, for your protection, answer “Yes.”
Why MFA Matters for Legal Professionals
Given the volume of malware transmitted through email, password recycling, password sharing, and other issues, most IT professionals consider MFA one of the most important security controls that can be implemented. According to Microsoft, MFA can help stop cyber attacks in their tracks, blocking 99%[1] of account-compromising attacks.
- Enhanced Security: MFA significantly reduces the risk of unauthorized access. Even if a password is compromised, the additional verification steps make it challenging for cybercriminals to breach your system.
As Bruce Schneier wisely noted, “Security is not a product, but a process.“
- Compliance: Many jurisdictions and regulatory bodies mandate stringent data protection measures. Implementing MFA can help ensure compliance with legal standards and avoid potential penalties. The American Bar Association’s (ABA) 2022 Legal Technology Survey Report highlights that 27% of law firms experienced a security breach, underscoring the need for robust security measures like MFA.
- Client Trust: Clients trust you with their most confidential information. Demonstrating your commitment to security through measures like MFA reinforces their confidence in your ability to protect their data. In a recent survey, 65% of clients indicated that they are more likely to choose a firm that prioritizes data security.
Remember, “Trust is the glue of life. It’s the most essential ingredient in effective communication” – Stephen Covey.
Implementing MFA in Your Law Firm
Transitioning to MFA doesn’t have to be daunting. Here are practical steps to integrate this vital security measure into your firm’s operations:
- Evaluate Your Needs: Assess which systems and accounts require MFA. Prioritize those with access to the most sensitive information.
Choose the Right Solution: There are various MFA solutions available, ranging from SMS-based verification to sophisticated biometric systems. Select one that balances security with user convenience.
As the saying goes,
The only secure computer is one that’s unplugged, locked in a safe, and buried 20 feet under the ground in a secret location…and I’m not even too sure about that one
Dennis Hughes, FBI.
- Educate Your Team: Ensure all staff members understand the importance of MFA and how to use it. Regular training sessions can help foster a culture of security awareness. According to the ABA, 72%[2] of law firms provide cybersecurity training to their employees.
Benjamin Franklin once said, “An investment in knowledge pays the best interest”
- Integrate Seamlessly: Work with your IT team or a cybersecurity consultant to integrate MFA with your existing systems. Ensure that the implementation process causes minimal disruption to daily operations.
- Monitor and Update: Cyber threats are constantly evolving and the next move by bad actors can’t be anticipated.. Regularly review and update your MFA systems to address new vulnerabilities and maintain robust security.
As Charles Darwin wisely noted, “It is not the strongest of the species that survive, nor the most intelligent, but the one most responsive to change.”
Stories About Why MFA Works
Let’s explore some scenarios that illustrate the importance of MFA and its effectiveness in real-world situations:
- The Case of the Compromised Password: Imagine an attorney at a mid-sized firm specializing in intellectual property receives a phishing email that looks like it’s from a trusted client. Unfortunately, they fall for the scam and enter their login credentials on a fake website. Without MFA, the hacker would have instant access to sensitive case files and client information. However, because the firm had implemented MFA, the hacker couldn’t get past the second layer of security—requesting a verification code sent to the attorney’s phone. The potential breach was thwarted, saving the firm from a major security incident.
- The Phishing Simulation: A law firm decided to test its employees’ vigilance by conducting a phishing simulation. They sent out a fake phishing email to see how many staff members would fall for it. Surprisingly, several employees clicked on the link and entered their credentials. This could have been disastrous if it were a real attack. However, since the firm had MFA in place, the additional authentication step blocked unauthorized access, and the firm used this as a learning experience to improve their cybersecurity training.
- The Lost Laptop Incident: Consider a scenario where a senior partner’s laptop, loaded with confidential client data, gets lost at the airport. Panic sets in as the potential for data exposure seems imminent. Thanks to MFA, even if someone managed to hack the laptop’s password, they would still need to verify their identity through the partner’s smartphone or biometric data. This extra security layer prevented unauthorized access and gave the firm time to remotely wipe the laptop’s data.
- Vendor Portal Protection: A large law firm uses multiple vendor portals for various services, each containing sensitive information. When a vendor’s system was compromised, the attackers attempted to use the stolen credentials to access the law firm’s portal. Fortunately, the law firm had MFA enabled on all vendor accounts, and the breach attempt was blocked by the second layer of verification. This not only protected the firm’s data but also reinforced the importance of requiring vendors to use MFA. This example illustrates that there are ways to avoid vulnerabilities caused by the mistakes of others.
Privileged Access Management (PAM)
Another acronym is PAM. Privileged Access Management (PAM) is another critical component of a comprehensive security strategy. PAM works through a combination of people, processes, and technology to give visibility into who is using privileged accounts and what they are doing while they are logged in. Limiting the number of users who have access to administrative functions increases system security, while additional layers of protection mitigate data breaches by threat actors. This concept was not new to me, but giving it a name has helped cement the knowledge in place.
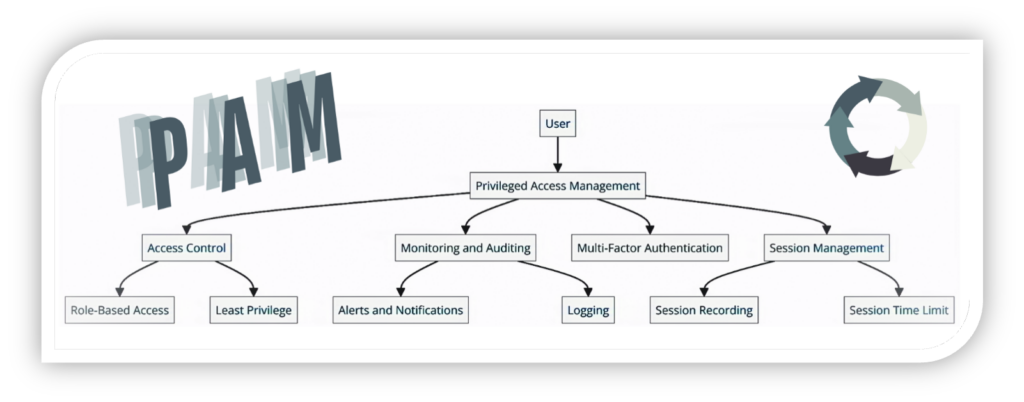
Examples of PAM in Action
Another way that helps me integrate new concepts or systems is to look at some scenarios that highlight how it works. Here are a few examples of how PAM effectively enhances security:
- The IT Admin Audit: At a large corporate law firm, IT administrators have access to sensitive data and critical systems. By implementing PAM, the firm tracks and records all activities performed by administrators. One day, unusual behavior is detected—an admin account is accessing data outside of normal working hours. PAM alerts the security team, who quickly investigate and discover that the account was compromised. The firm takes immediate action to revoke access, reset passwords, and secure the affected systems, preventing a potential data breach.
- Limiting Access in a Merger: During a merger between two law firms, only a select few need access to the most sensitive financial and client data. By using PAM, the firm ensures that only the necessary personnel have access to this information. Each access attempt is logged and monitored, providing a clear audit trail. This visibility helps in maintaining strict control over who accesses sensitive data, ensuring the security and confidentiality of the merger process.
- Securing Remote Work: As remote work becomes more prevalent, a mid-sized law firm deploys PAM to manage and monitor privileged access. With PAM, they can enforce policies that restrict access based on location and device. For example, if an employee tries to access the system from an unrecognized device or location, PAM requires additional verification or denies access altogether. This reduces the risk of unauthorized access from compromised devices or unfamiliar locations.
Conclusion
In an era where cyber threats are a constant concern, Multi-Factor Authentication and Privileged Access Management stand out as critical defense mechanisms. For legal professionals, implementing these measures is a proactive step toward protecting sensitive data, ensuring compliance, and maintaining client trust. Don’t wait for a breach to happen; strengthen your security today with MFA and PAM, and safeguard your firm’s future.
By embracing MFA and PAM, you not only protect your practice but also demonstrate a commitment to the highest standards of security and client care. Remember, in the realm of cybersecurity,
An ounce of prevention is worth a pound of cure.
Benjamin Franklin.
Implementing these security measures might seem like a hassle, but consider the alternative: trying to explain to your clients why their confidential information was leaked. It’s a no-brainer!
As humorist Will Rogers once said, “Even if you are on the right track, you’ll get run over if you just sit there.”
So, let’s get moving and secure our digital frontier with MFA and PAM!
Other articles and blogs:
- What Is Multi-Factor Authentication (MFA)? – How-To Geek – https://www.howtogeek.com/343078/what-is-multi-factor-authentication-and-why-should-i-care/
- Multi-Factor Authentication (MFA) Explained in 5 Minutes or Less – Geekflare – https://geekflare.com/multi-factor-authentication/
- What is Multi-Factor Authentication? – The Conversation – https://theconversation.com/what-is-multi-factor-authentication-and-how-should-i-be-using-it-159944
- A HOW-TO-GUIDE FOR MULTI-FACTOR AUTHENTICATION – CISA – https://www.cisa.gov/sites/default/files/publications/NCSAM_MFAGuide_2020.pdf
- Privileged Access Management (PAM) Overview – CyberArk – https://www.cyberark.com/what-is/privileged-access-management/
- Privileged Access Management Explained – Varonis – https://www.varonis.com/blog/privileged-access-management
Notes
[1] Microsoft’s MFA effectiveness study: Blocking 99% of account-compromising attacks
[2] American Bar Association’s (ABA) 2022 Legal Technology Survey Report: ABA Legal Technology Survey Report
Assisted by GAI and LLM Technologies per EDRM GAI and LLM Policy.


