Single-Tenant Architecture: A New Paradigm for Cloud Security

Alarm bells rang when several respected ediscovery providers announced they had shut down their sites due to security breaches. The causes were different for each, but the results were the same. Clients across hundreds of sites could not access data for days or weeks.
In a multi-tenant environment, security breaches often place data across client sites at risk. If a hacker uses ransomware to encrypt a shared storage device, everyone loses access to their data (at least until the ransom is paid). If a cyber terrorist can break into a provider’s domain controller and steal user credentials, every site is suddenly at risk.
The problem stems from the traditional moat and castle architecture I have written about in the past. When the barbarians get past the proverbial gates, whether through an insider or weak defenses, they typically have the run of the castle. Everyone behind the walls is at risk.
But aren’t multi-tenant sites the standard for our industry? In the data center era, the answer was yes. You would be crazy to set up individual sites for each client when you had to buy servers and pay for cages to house them. The cost to buy, install and manage hundreds of servers and create individual security environments for each was too high.
That isn’t necessarily the case in the cloud. Companies like Amazon, Microsoft and Google sell virtual instances and raw computing power by the second, allowing hosting providers to build single-tenant systems that are safer and, ironically, less expensive than the older multi-tenant systems. They also support newer utility pricing models that allow clients to pay by the hour for the services they use rather than by the month. The savings to be garnered are substantial, but the benefits of greater security in a single-tenant environment go well beyond basic hosting costs.
Let me explain what I mean.
Single vs. Multi-Tenant Architecture
In recent years, many vendors moved their infrastructure to the cloud. In doing so, most simply “forklifted” their systems onto equivalent cloud servers. In essence, they treated the cloud like another data center, replicating the data center architecture that served them well. And, importantly, they continued using multi-tenant architecture for client sites.
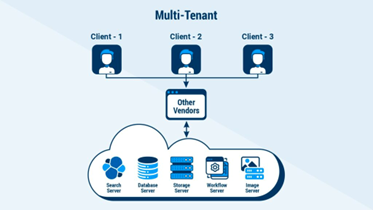
The problem with this approach became obvious when the industry started experiencing security breaches. If the site supports multiple clients in a shared environment, security becomes a function of the weakest link. If one client adopts lax security procedures, a hole is opened in the castle’s wall, potentially affecting everyone inside. If a user on one client site falls for a phishing scam and credentials are compromised, the risk of a multi-site breach grows. The attack vector could come through that client’s site, opening the target up through the back door.
This could be especially critical for a company hosting particularly sensitive data.
In contrast, single-tenant sites are like single-tenant castles. If there are hundreds of castles in the cloud, a breach of one doesn’t mean a breach of all. Only one client’s data is affected, the rest are isolated and secure in their own “Virtual Private Clouds.”
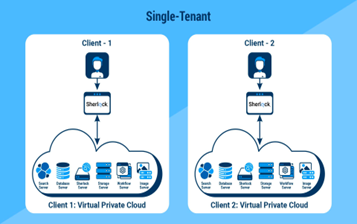
Likewise, if one client is more lax with security, others aren’t needlessly put at risk. Equally important, single-tenant architecture allows individual clients to customize site security commensurate with the nature of the hosted data.
Thus, a single-tenant environment provides increased flexibility for security-sensitive applications along with customizable security options. It also gives a client the ability to host data anywhere in the world, including in its own cloud environment. A single-tenant environment means that documents, data and even the virtual servers all reside within a single, secure environment.
Single-tenant architecture provides other advantages as well. First, it allows clients to size the site according to their needs, quickly adding servers when necessary or dropping them as requirements wane. And, should the data require HIPAA or GDPR compliance, it doesn’t matter where the service provider is located. The sites can be situated anywhere in the world.
But What About the Cost?
The obvious question to ask about single-tenant architecture is about cost. If the whole purpose behind multi-tenant architecture was to save on computing and operational costs, why is that any difference in the cloud?
The answer is simple. Cloud computing is based on a different paradigm than data centers and individual hardware. You don’t buy servers and install them in cages in the cloud. Rather, you rent computing power and virtual servers by the second, paying only for what you use, when you use it.
In the cloud, you can spin up a single-tenant site in about three minutes, providing a dizzying array of computer power at your fingertips in about the time it takes to get a cup of coffee. You use the site for a few hours and then shut it down for the rest of the day. The cost for this usage is the cost to run the computing power needed–not for the month but only for the hours needed. When the site is turned off, the only cost remaining is for data storage, which is a fraction of the cost of running an active server environment.
You can even schedule operating hours for a single-tenant environment, configuring the site to turn off after business hours and turn on when the day begins. Or use bots to watch site activity, and automatically turn servers off when not in use.
In contrast, multi-tenant sites have to run 24/7 because different users work on different schedules. If one user on one site needs to access the site at three in the morning, the entire site has to remain online. And, the costs to keep a large, multi-tenant environment running throughout the month eclipse the costs to keep individual sites running when you need them. There are 730 hours in a month. How many hours is your team actually using a typical ediscovery site? Why pay for more?
The public cloud has ushered in a new era for computing that is based on renting computing power rather than buying it. In this new era, security risks associated with multi-tenant architecture may no longer be necessary. Instead, with a single-tenant design, you can build your own castle, protecting it as you see fit. And, with utility pricing, the castle is online only when you need it, not the entire month.
It’s a new paradigm for cloud security, one that can solve real problems.


