[EDRM Editor’s Note: EDRM is happy to amplify our Trusted Partners news and events. The opinions and positions are those of Gretchen Ruck.]
Defining the role of inherent risk in cybersecurity
Inherent risk is a concept that while fundamental to cybersecurity, has largely been disregarded by popular cybersecurity risk guidelines and standards and remains arcane to the vast majority of cybersecurity practitioners. Inherent risk is all about the BIG picture, it’s nearly impossible to examine the relationship between cybersecurity strategy and business priorities without taking inherent risk into perspective.
Inherent risk is all about the BIG picture, it’s nearly impossible to examine the relationship between cybersecurity strategy and business priorities without taking inherent risk into perspective.
Gretchen Ruck, Lockhaven Solutions.
Inherent risk in an invaluable tool for security teams for facilitating meaningful dialog with business leaders and other non-technical stakeholders to build consensus on the top risks in which a failure to safeguard IT systems or protect sensitive information would be the most devastating to a business. You can define it as, “The risk to an entity in the absence of any direct or focused actions by management to alter its severity.” It might be easier to understand inherent risk by thinking about saying, “think globally and act locally”, as illustrated below.
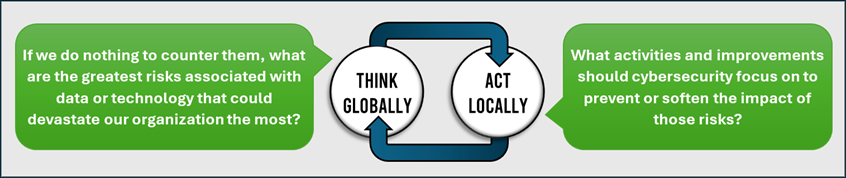
While I can’t say that adding an inherent risk perspective is going to solve all of your security challenges, although that would be awfully nice, but it may help you:
- Engage leaders better by using business terminology to reach consensus on your top cyber risks,
- Grow a stronger sense of cyber-literacy amongst key influencers and decision makers,
- Demonstrate that cybersecurity is more than a cost center, it’s a value center,
- Develop a risk-aware culture where departments consult with cybersecurity, not avoid it, and
- Improve ability to evaluate and adopt new technologies and adapt to new market trends.
Inherent cyber risk – why it’s such a tough concept to understand
While that definition seems clear and concise, it’s also woefully unhelpful to practitioners seeking tools or job aids to help them identify and prioritize actual inherent cyber risks. This leaves many practitioners searching the National Institute of Standards & Technology’s Cybersecurity Framework (NIST CFS) and the FAIR Institute for help.
In the recently released, long-awaited version 2.0 of the NIST CSF, more focus is given to governance and risk activities, yet the concept of inherent risks has only one brief cameo. Control ID.RA-05 within the NIST CSF mentions that “threats, vulnerabilities, likelihoods, and impacts are used to understand inherent risk and inform risk response prioritization”, without defining what “inherent” means or how to effectively apply it.
Another approach to measuring cyber risk is from the Factor Analysis of Information Risk (FAIR) Institute. Similar to NIST, FAIR describes inherent risk as the amount of risk that exists in the absence of controls, in contrast to residual risk, which is the amount of risk that remains after controls are accounted for.[1] After introducing this concept, FAIR provides a working definition of inherent risk as the “current risk level given the existing set of controls rather than the hypothetical notion of an absence of any controls.”[2] What they describe in their working definition isn’t inherent risk, it’s what’s known as “a priori” risk, which isn’t the same thing.[3]
So why are inherent risks often disregarded? Our belief is that contradictory definitions have led to confusion and avoidance of the topic. Cybersecurity can seem chaotic and expansive, with an overwhelming number of recommended guidelines, best practices, and regulations in place to protect against any number of countless threats. Also, in a landscape of competing business concerns, cyber risk is often a lower priority, failing to attract the attention of the board or senior business leaders.
As cybersecurity matures within an organization, it shifts from being driven by the primary concern for compliance to a technology risk perspective, and then ultimately should strive to focus on the value that cybersecurity provides.
Gretchen Ruck, Lockhaven Solutions.
Managing inherent risks should be a key cybersecurity strategy objective
As cybersecurity matures within an organization, it shifts from being driven by the primary concern for compliance to a technology risk perspective, and then ultimately should strive to focus on the value that cybersecurity provides, which is ingrained in determining inherent risks. Drawing from my experience as the parent of a toddler, I’d like to impart an alternative perspective on how this shift can change how we frame the messages that we share with our stakeholders.
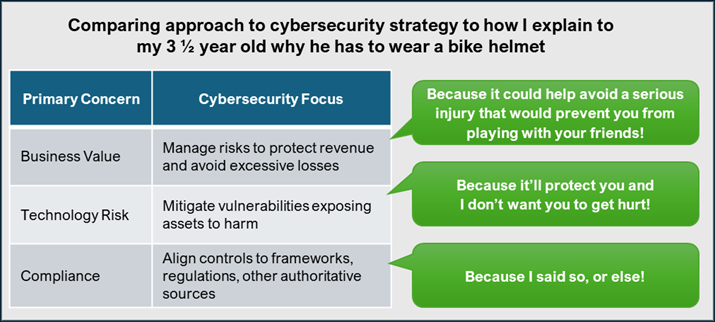
A robust cyber strategy should articulate the alignment between inherent cyber risks and the broader business. It’s essential for an organization’s cyber strategy to communicate how the priorities, responsibilities, policies, and budget decisions of cybersecurity leaders contribute to managing these risks effectively.
The importance of conveying the relationship between cyber strategy and inherent risks is not entirely lost on regulators. As an example, in New York, companies that maintain financial accounts in the state are required to ensure that Chief Information Security Officers (CISO) explain cyber risks to the board of directors in a manner that allows them to exercise oversight of cyber risks.[4]
Inherent cybersecurity risk model overview
The following model is based on extensive experience interacting with non-technical business stakeholders such as board directors, investors, executives, and governmental oversight authorities. It represents an approach that seeks to bridge the communication gap between the decision-makers, who shape the direction of the business, and operational leaders focused on delivering results.
This model seeks to facilitate a meaningful dialog between business leaders, investors, and attorneys, and cybersecurity practitioners and technical experts; to build consensus on the top risks in which a failure to safeguard IT systems or protect sensitive information would be the most devastating to a business.
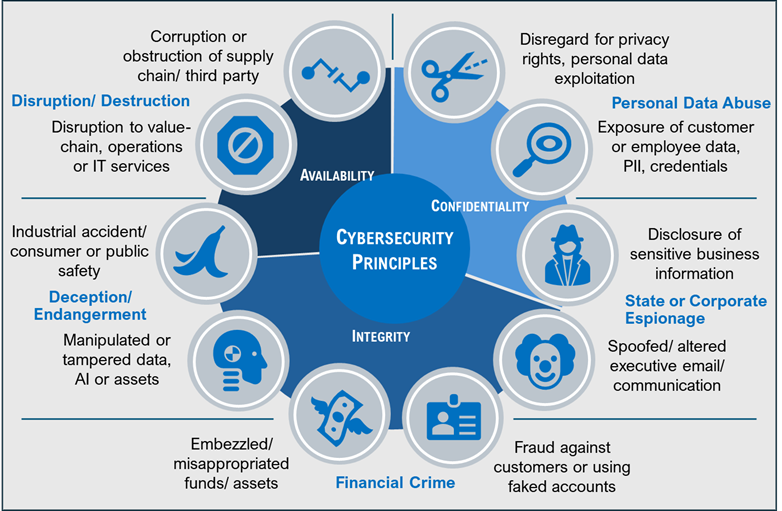
Five risk categories are identified that present challenges to businesses. These challenges will vary in importance depending on the services they provide and how they’re delivered. In the figure that follows, these categories are aligned to the three core cybersecurity principles of confidentiality, integrity, and availability.
- Disruption/ Destruction – Disrupting business operations or destroying or restricting the means of production
- Deception/ Endangerment – Altering data, manipulating assets, or influencing outcomes to instigate deception, distress, or harm
- Financial Crime – Stealing money or valuable goods from the company, its customers, or business partners
- State/ Corporate Espionage – Harming the business’s competitiveness by reputational damage or stealing trade secrets
- Personal Data Abuse – Failing to protect stakeholders and individual rights by exposing or mishandling sensitive, personal information
As illustrated below, each category is divided into two broadly defined scenarios, which become the starting point to discuss the challenges most critical to industries or verticals, and also, more narrowly, individual organizations.
How to identify and measure inherent risks
This process doesn’t need to take months to complete; in fact, it can be the quickest way to understand a company’s risk level to help evaluate critical business decisions. To begin the process of determining your company’s inherent cyber risks, pick three to five risk scenarios that seem to align the closest to your industry.
While perhaps not a perfect fit, an Industry Risk Profile, examples of which are found in the figure below, can be used as a starting point for companies sharing factors such as anticipated threats, operating model, and regulations. Next, the organizational profile can be customized and detailed through a risk analysis process. The risk scorecard will focus on managing those top three to five risks.

Based on competitive positioning, revenue generation priorities, and the business model, consider in which scenarios would technology issues or data exposure be riskiest to your business. This allows us to focus on the activities and assets that are the most critical for your business to protect and on what improvements to focus your cyber spending.
Risk scenarios are ordered based on risk level as represented by exposure to loss and damage. Prioritize scenarios based on the severity of potential damage that could result from the occurrence of a risk event. Consider how the evolving landscape of technology could impact risk, for example you may want to reflect on how Artificial Intelligence (AI) will make risk events harder to detect, more challenging to prevent, easier to develop, quicker to execute, and more precisely targeted at potential victims.
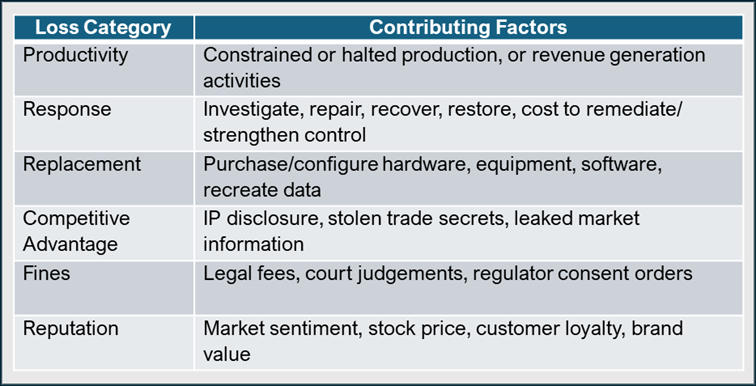
When crafting your cyber strategy, focus on identifying which risk scenarios are most harmful to your business model. To illustrate this, in the table below I’ve described some of the potential risk events for three of the previously discussed risk scenarios.
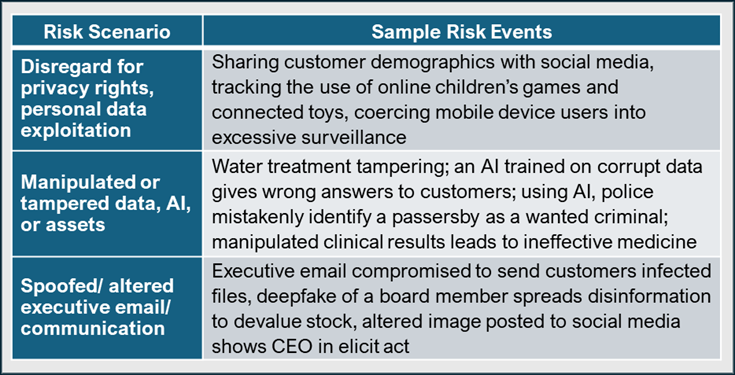
Keep your descriptions brief, bound to manageable options, and as non-technical as possible to help ensure that they can be understood by a diverse group of stakeholders. The following types of loss may be used as guidance to identify and describe risk events in terms of the types and extent of damage and loss that can be expected. These types are based on FAIR, Forms of Loss.[5]
Next steps – how to apply this model
Here are five actions that every CEO and CISO can prioritize.

This process is often facilitated by external, third-party firms that specialize in cyber risk analysis. While consultants can help guide organizations through the process of identifying and prioritizing risks, it’s vital to remember that company executives and board members hold ultimate responsibility for deciding how best to manage those risks.
It’s essential to choose a partner who treats this process as collaborative, engaging participants through a shared journey. When done correctly, it’s rewarding to witness non-technical executives and board members become much more comfortable asking questions about cybersecurity as they demonstrate mastery of the concepts described in this paper.
Notes
[1] FAIR references the term “controls” which are the collective set of software tools, system configurations, administrative, and operational activities, policies and procedures, training and education, and user responsibilities that play a role in helping to safeguard the technology and protect the data on which the business relies.
[2] Measuring and Managing Information Risk: A FAIR Approach
[3] https://iep.utm.edu/apriori/
[5] Measuring and Managing Information Risk, A FAIR Approach, by Jack Freund and Jack Jones, in chapter 4, FAIR Terminology, section titled Forms of Loss, published by Elsevier in 2015, ISBN 978-0-12-420231-3
Assisted by GAI and LLM Technologies per EDRM GAI and LLM Policy.


